Website penetration testing is a commonly used security testing technique for monitoring web applications and resolving vulnerabilities. It also helps end-users in understanding the perspective of hackers and the ease of accessing sensitive data, the penetrability of email servers, and the overall security.
It’s important to understand the differences between online website penetration testing and vulnerability assessments in terms of resolving security issues. While the latter allows you to find out the known weaknesses within an application, the former provides you with the methodology and testing tools to exploit the weaknesses and find out their true impact.
Web Penetration Testing Methodology
Proceeding with the web penetration testing procedure with a fixed number of steps ensures that all the important areas are covered and the right kind of attack methods are devised.
1. Reconnaissance

Gathering information about the system/application allows the testing team to prepare a list of potential vulnerabilities and understand the areas of breach. This will also help in understanding the kind of testing approaches required, the tools needed, and the mode of testing. The kind of testing environment should be understood for gaining perspective about the firewalls used, security protocols that may need to be disabled, or proxies to be changed for testing browsers.
The information gathered can also be used to formulate the scope of testing since all aspects of the web application cannot be covered otherwise. The next step is to make all the necessary documentation available to the testing team in order to understand the business logic, integration points, infrastructure map, web services, etc. There are certain HTTP/HTTPS protocol basics that one must be aware about along with the methods of traffic interception for proceeding with the testing process.
Always set in place certain criteria for determining the success of the procedure. For this, you can also use results from previous tests, the vulnerabilities discovered previously, and the remediation solutions taken up.
2. Testing

The actual testing procedure can be conducted from any location after ensuring that there are no restrictions on any port or service by the internet service provider. Play with different user roles and run a test based on each of them to uncover specific vulnerabilities. The system may behave differently in each context and this must be captured for testing privilege escalation possibilities. The success criteria can be used in this context to evaluate the progress of the procedure and report vulnerabilities according to the defined process.
Here, the tester must also look into the steps to be taken after the system has been compromised during the testing procedure. All of the findings, details on the vulnerabilities discovered, and the remediation suggestions will be compiled into a report, both on an intermediate basis and as a final report. This is to ensure that the concerned stakeholders are involved in the penetration testing process through a well-defined communication portal.
3. Post-Testing

Once the reports and details about the testing procedure are shared with the concerned stakeholders, the next step is to dive into the remediation procedures. Stopping at the discovery of vulnerabilities isn’t fully helpful and findings should be discussed and implemented based on the criticality of the vulnerability. Some companies offer the option of retesting vulnerabilities after the steps for remediation are implemented to ensure that they are properly fixed. Finally, whatever changes were made to the system, such as changes in proxies, should be set back and cleaned up for daily operations.
Types of Website Penetration Testing
There are mainly two types of website penetration testing procedures wherein the vulnerabilities need to be detected and resolved.
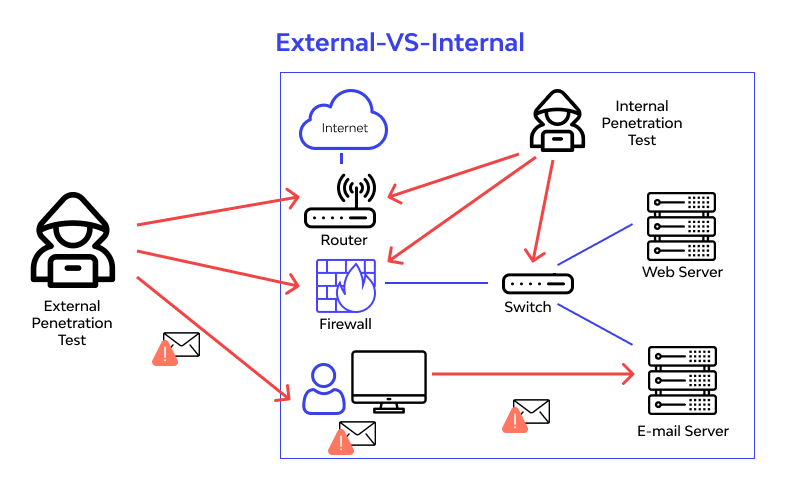
- Internal Penetration Testing
This kind of testing is done within the system over the LAN and involves testing web applications through the intranet. There is a high probability for vulnerabilities within the corporate firewall which can lead to the leak of sensitive information. Internal testing covers the possibilities of accidental or intended malicious activities from employees or flaws within the system. It covers a wide range of attacks including social engineering, unprotected employee credentials, phishing via email/phone, privilege escalation, manipulation of unlocked terminals, etc.
- External Penetration Testing
These are external attacks that probe for an entry into the system from outside. Testing teams use information on the IP address of the targeted web application and then search and scan public webpages. With this, they find information on the target host and use different techniques to compromise the security. It also includes testing servers, firewalls, etc.
This article provides a basic idea about website penetration testing, different types of the procedure, and the methodology followed for a successful testing procedure. It’s equally important to select a third-party service provider with enough experience, adaptability, and skill sets for engaging in the procedure and staying through the remediation phase. They must also have the qualifications and credentials for modifying the testing procedure in accordance with the compliance requirements of each industry.





